Accountable Governance

Information Security
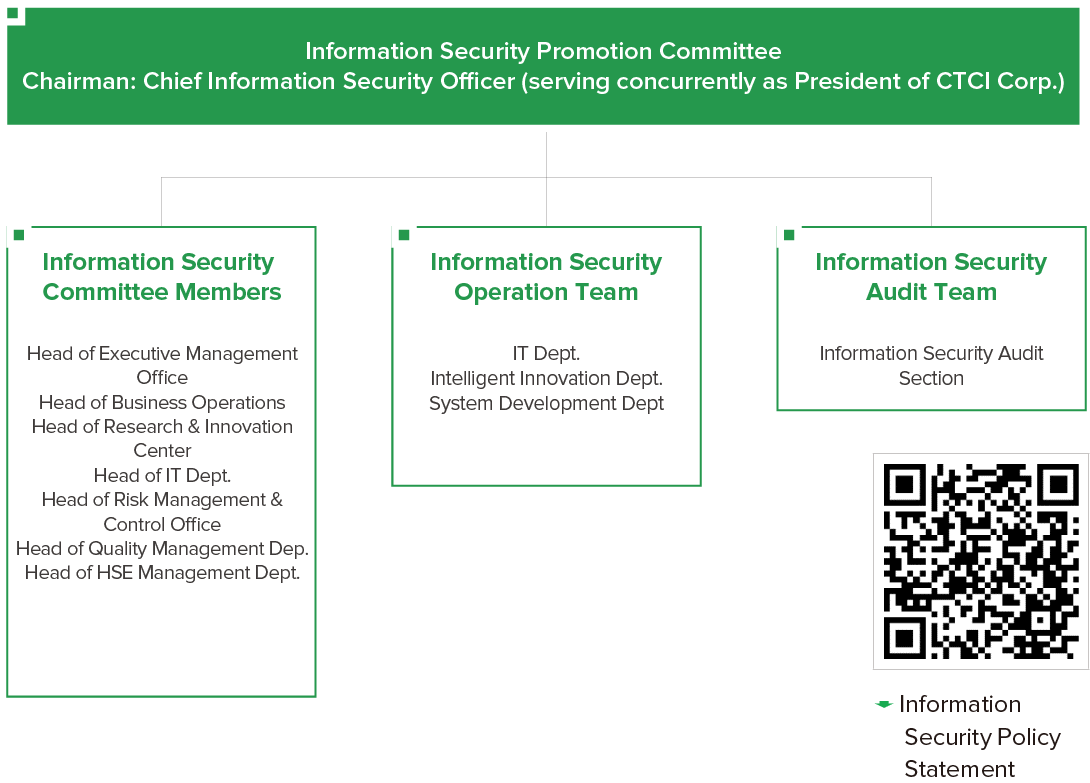
Information Security Governance and Organization
The role of information security is crucial to the operation of CTCI. Therefore, CTCI has incorporated information security into the company's overall risk management framework and established the Information Security Promotion Committee, with the President of CTCI serving as the committee chairman to issue Information Security Policy Statement as the the foundation of promoting ISMS. In terms of execution, the Information Security Promotion Committee is responsible for formulating information security objectives, strategies, and management procedures. At least once a year, the committee convenes an Information Security Management Review Meeting to review information security management matters, conduct a risk assessment report, and review risk treatment plans. Additionally, recognizing the increasing importance of information security and to comply with the requirements of Taiwan's Financial Supervisory Commission for secondary exchange listed company, CTCI has established an Information Security Audit Section under the Information Security Promotion Committee to carry out IT audit operations. Such mechanism ensures effective operation of the ISMS, helps strengthen internal risk control, and continuously enhances information security capabilities, thus ensuring compliance with regulations and protect business continuity.
Information Security Management and Control Measures
CTCI deeply understands the critical importance of avoiding any lapses in managing information security risks. Therefore, we continuously strive for improvement by employing the PDCA (Plan-Do-Check-Act) management system cycle to ensure effective implementation of risk control. Additionally, we enhance the effectiveness of information security management through three key initiatives: expanding skills, initiating change, and sharing knowledge.
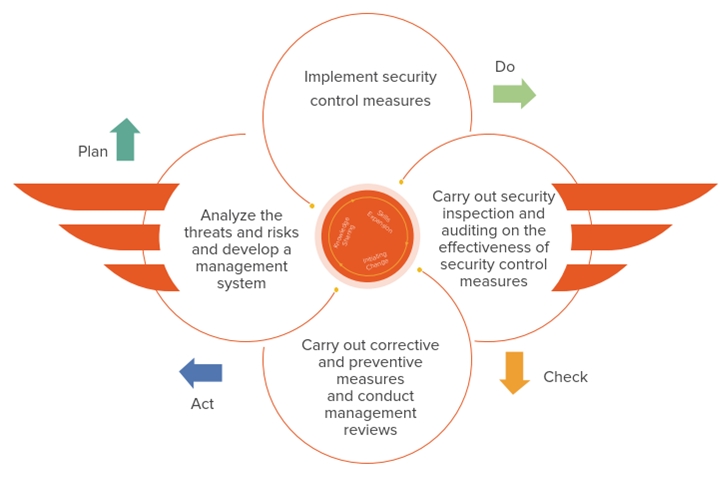
ISMS implementation cycle of CTCI - The management cycle of information security system

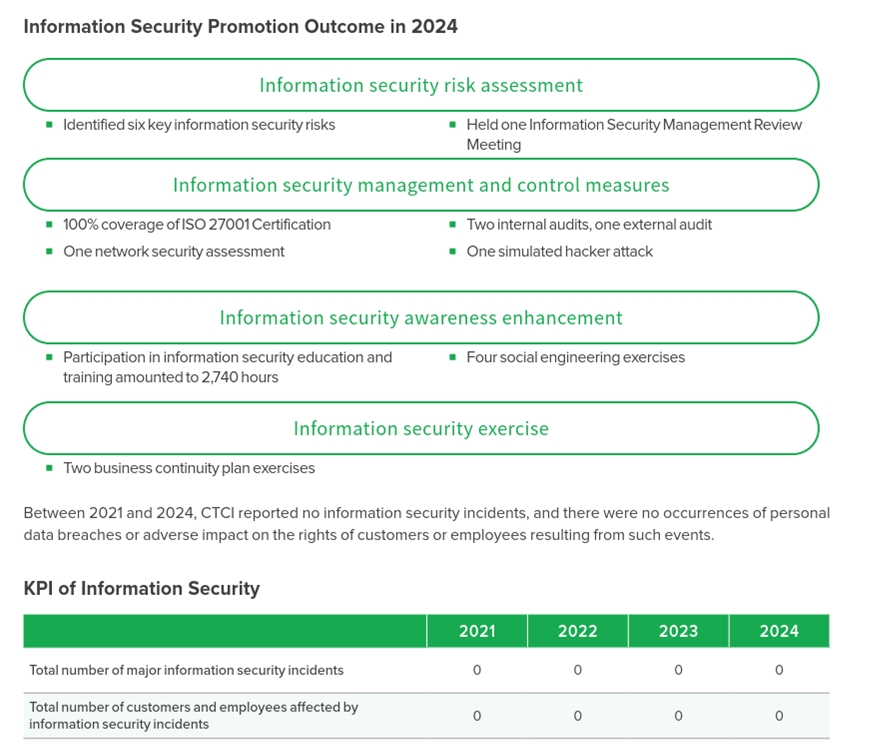
Information Security Risk Assessment
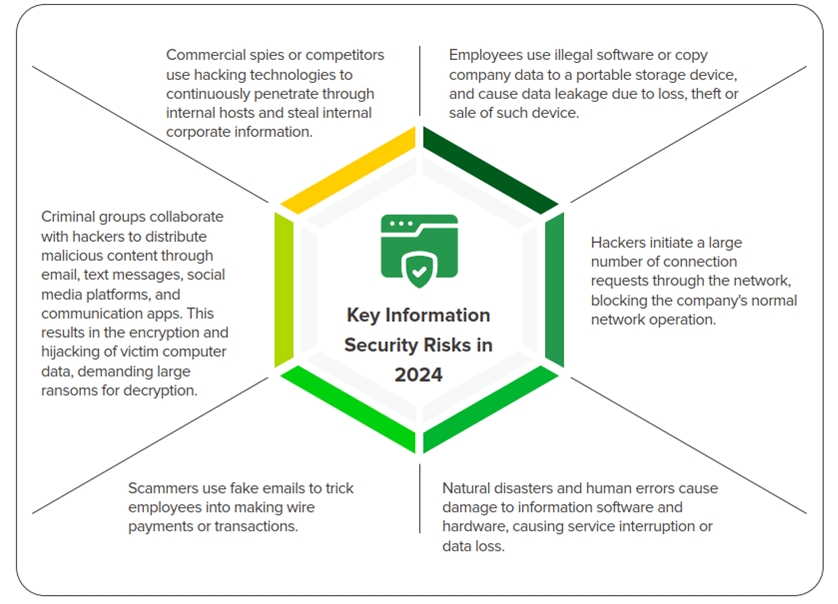
CTCI has formally integrated information security into its overall risk management framework and conducts information security risk assessments at least once a year. For risks exceeding acceptable thresholds, CTCI would propose risk response plans and take measures to manage risks to continuously monitor and ensure improvement.
ISO 27001 Certification
To ensure information security and business stability, CTCI has established a comprehensive management system in accordance with ISO 27001. In 2023, CTCI obtained ISO 27001 certification for its Information Security Management System (ISMS), valid through 2025 (the certification body is SGS). To ensure continued alignment with international standards, the company undergoes annual surveillance audits conducted by third-party certification bodies, continuously strengthening the effectiveness of information security governance and the quality of its management practices. As part of its commitment to the effective operation and continuous improvement of its IT infrastructure and ISMS, the company conducts internal audits semi-annually in line with ISO 27001 requirements. These audit results help identify potential risks and provide recommendations for improvement, enabling timely optimization and further reinforcing information security governance and overall operational resilience.
Information Security Awareness Enhancement
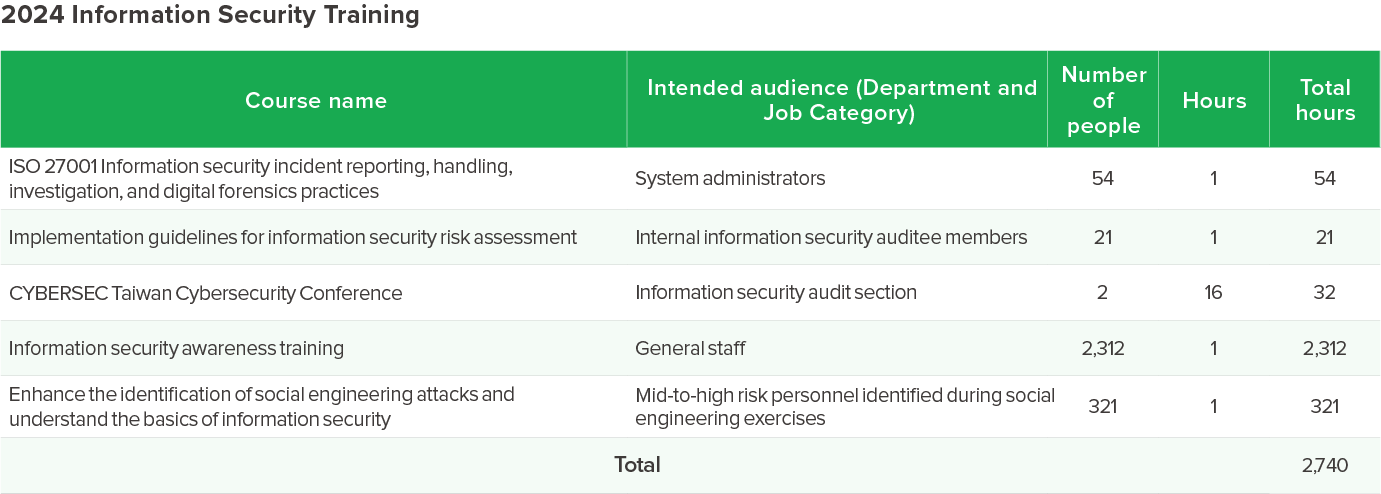
In response to the constantly evolving information security threats and tactics, CTCI continues to enhance the information security awareness of its colleagues. In 2024, the Company conducted information security training for both IT Department staff and employees in general, totaling 2,740 hours. Professional information security training included ISO 27001, covering information security incident reporting, handling, investigation, and digital forensics practices, as well as information security risk assessment and participation in events such as the CYBERSEC Taiwan Cybersecurity Conference. General information security training covered topics such as recognizing social engineering attacks and information security focus, as well as reinforcing information security concepts among CTCI colleagues.
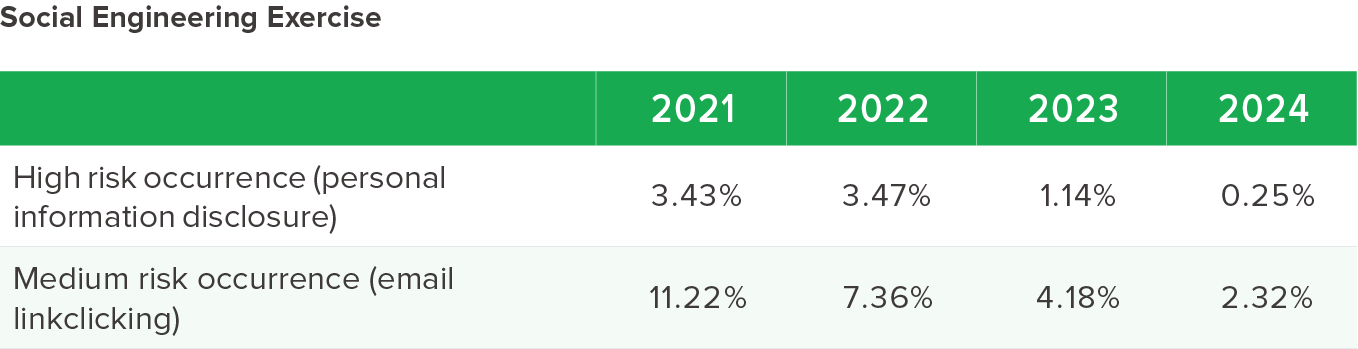
Outcome of Information Security Promotion
CTCI remains committed in promoting information security, firmly adhering to the four main objectives laid out in its information security policy. The Company puts effort in safeguarding the confidentiality, integrity, and availability of information. The effort not only reflects CTCI’s strength in the field of information security, but also highlights its high regard and commitment to corporate operations and the client’s information security.