Technology
技術分享
Applying IoT Technology to Engineering Management
— Tai-Yuan Chang, Assistant Chief Engineer, Group Research & Innovation Center, CTCI Corporation, Group Engineering Business
For CTCI, an engineering, procurement, and construction (EPC) company, the key to making EPC intelligent— or iEPC for short— lies in the adoption of information technologies, the first step of which is to build an environment conducive for Internet of Things (IoT). IoT is about connecting various "objects" that have built-in sensors in a wireless or wired manner, so that the information collected from these objects can be monitored, processed, and analyzed to create a safe and comfortable workplace environment. This article will first explain the principles and characteristics of various key IoT technologies before delving into the work of CTCI’s Group Research & Innovation Center, which has been using IoT technologies to make construction site management more intelligent.
IoT composition architecture
The IoT architecture (shown below) includes three layers from the bottom-up: sensing layer, network layer, and application layer. Sensing layer includes four components: sensing objects at the end, sensors, sensing area network, and gateway. Network layer is mostly TCP/IP network or mobile communication network. Application layer is about application systems built by enterprises in response to various business needs.
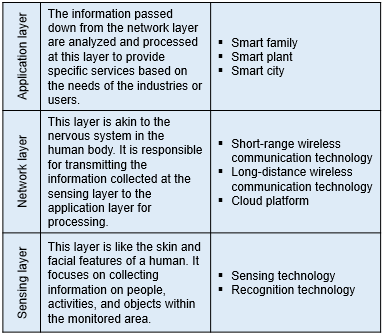
IoT architecture
Each layer serves different function. The main task of sensing layer is to obtain information about the object(s). The information is then accurately transmitted to the information platform through the network layer with appropriate wireless communication network technology. Next, the information will undergo analysis and calculation, so that it can be connected with the systems in the application layer to control the future actions of the object(s). Now we turn to look at some of the critical technologies involved in each layer.
I.Key technologies in sensing layer
There are two technological aspects in the sensing layer: "sensing technology" and "recognition technology." Sensing technology involves installing sensors on desired objects so that the objects have the capability to sense changes in the environment or object movement. Then the collected information is uploaded to cloud platforms via internet. The function of these sensors is akin to human sensory organs, which detect physical changes in the surrounding environment and convert them first into analog electrical signals, then into digital signals for subsequent computer processing. The primary sensor types are as follows:
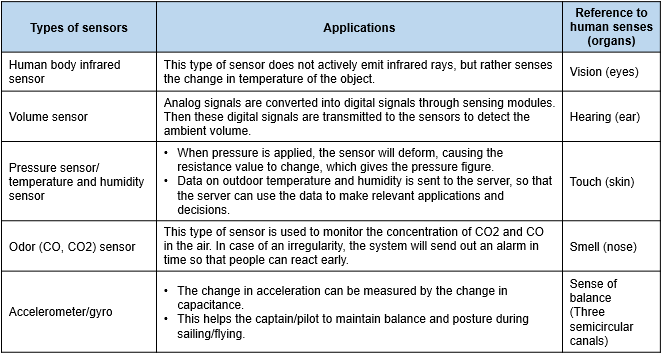
Common types of sensors
As for the recognition technology aspect, this helps quickly recognize an item’s identity, such as item name, origin of production, date of manufacture, and manufacturer. The following are the primary types of recognition technology:
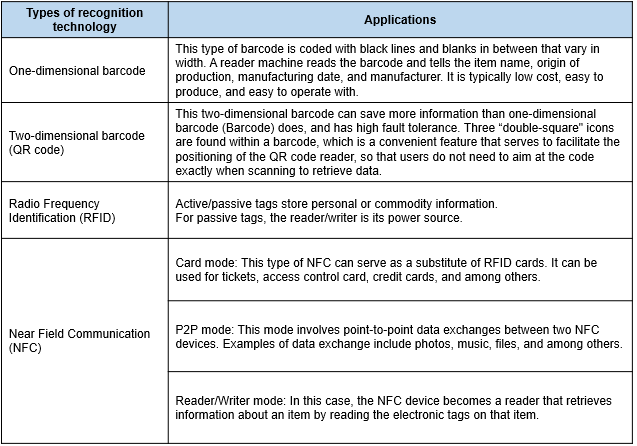
Common types of recognition technologies
In short, sensing and recognition technologies in the perception layer allows us to collect important information about the detected objects in the physical world, such as event, time, place, and status.
II.Key technologies in network layer
Wireless communication networks come in all sorts of communication ranges and transmission rates. Generally, wireless networks can be classified as "short-distance wireless communication networks" and "long-distance wireless communication networks." The purpose of these types of communication is to connect to the cloud on the network. The figure below indicates the classification of wireless communication protocols.
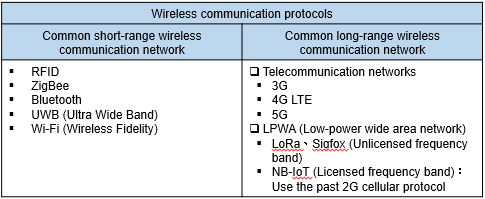
Types of wireless communication protocols
Short-distance wireless communication networks are also known as local area networks. The best examples include ZigBee, Bluetooth and Wi-Fi. Generally speaking, Wi-Fi has a transmission distance of around 100m, 30m for ZigBee, and 20m/50m for Bluetooth 4.2/5.0. The transmission range of less than 100m makes this type of network ideal for application in a place where space is limited but a lot of devices need to be controlled, such as factories. This type of network is known for stable frequency bands and fast communication speeds. Its drawback is that devices consume large amount of power. However, devices are now gradually being designed to be more energy-saving in recent years. As for UWB (Ultra Wideband Technology), it is not suitable for use in construction sites and will not be discussed here because it requires directional antennas and an Ethernet power supply line (Power Over Ethernet, POE) to be widely installed either in indoor or outdoor fields. In that case, signal transmissions are vulnerable to metal shielding and may become weak. For a comparison between various short-range wireless communication protocols, see the following chart.
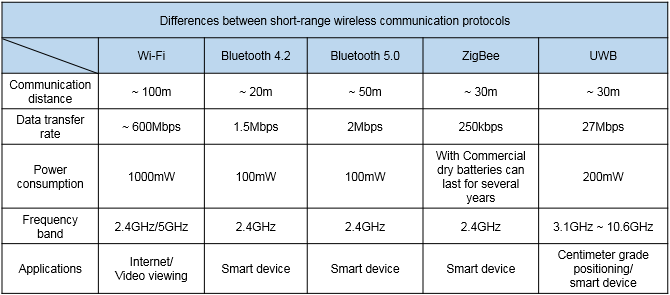
Differences between short-range wireless communication protocols
Long-distance wireless communication networks are known as external networks. The best examples include 3G, 4G LTE, and LPWA, which has attracted attention in the IoT world in recent years. Here, we will first explain the telecommunications network communication technology. 3G/4G LTE, which should be familiar to everyone, is comprised of base stations and handheld devices. Users can perform voice or data transmission as long as they are within the coverage of a base station’s communication. It contains three layers from the bottom-up (shown below): mobile phone→base station→switch in the telecommunications room.
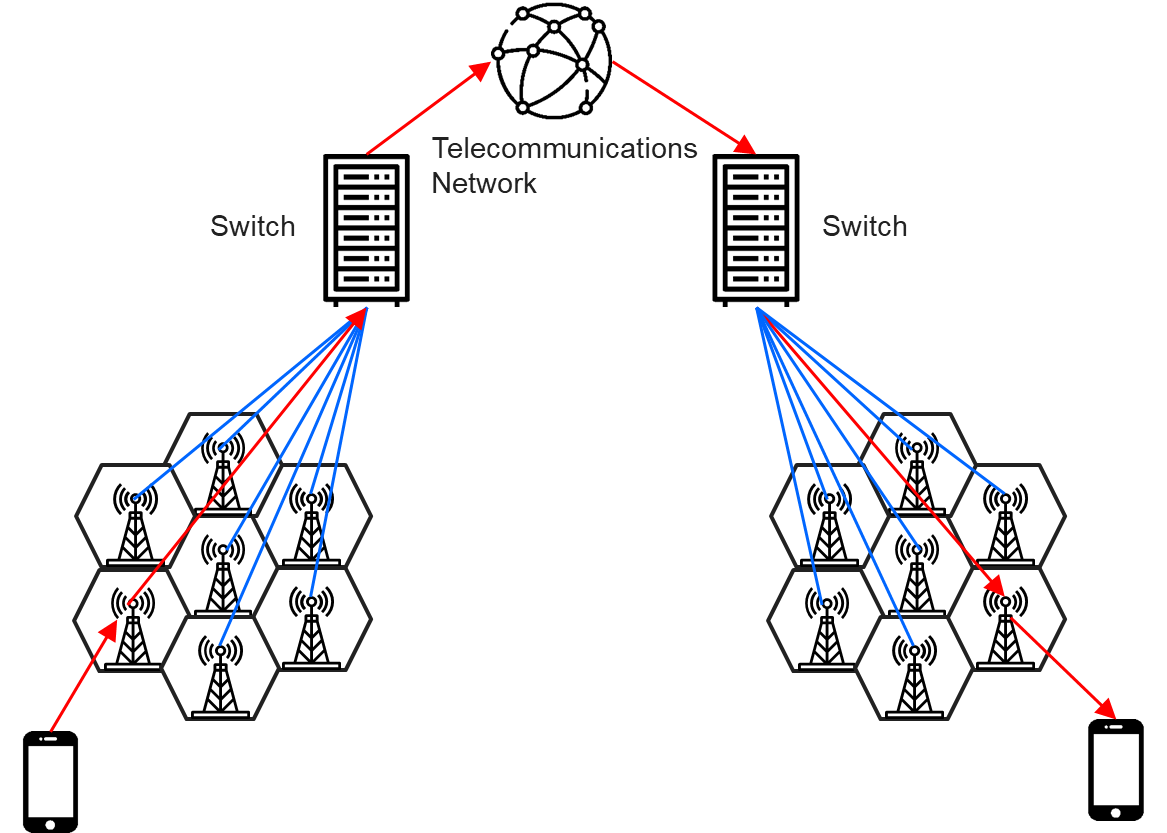
Telecom network architecture
As for 5G (fifth generation communication technology), which has gained popularity in recent years, it is the next generation of mobile communication network technology, featuring low latency (URLLC), large bandwidth (eMBB) and wide connection (mMTC). The derived Open RAN technology can be extended and applied to "enterprise private network." Since this has nothing to do with our discussion here, we will not delve into the evolution of telecommunication network communication technology, and will rather focus on LPWA. As IoT market continues to grow, all sorts of Low Power Wide Area (LPWA) networks have been developed, including LoRa, Sigfox, NB-IoT, among others. The common feature is that they can reach hundreds of meters in terms of communication range. They have deep/wide coverage, low power consumption, and massive connections. The following figure shows the correlation between long/short distance wireless communication distance and battery consumption.
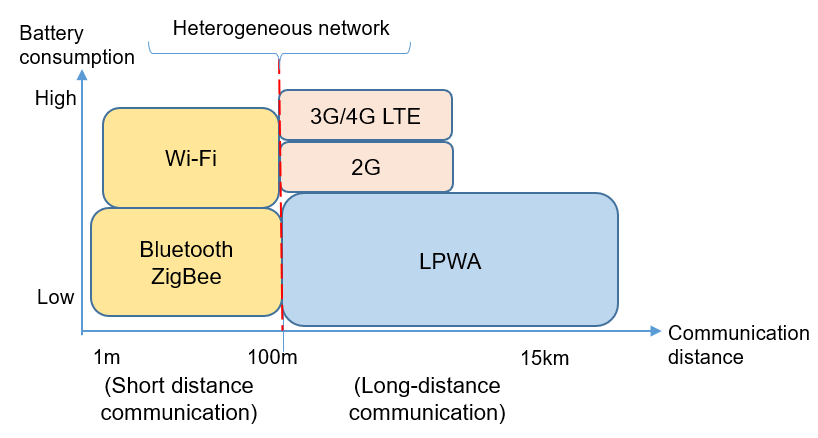
The relationship between long- and short-distance wireless communications and battery consumption
A key trait of IoT is maintaining continuous transmission of a small amount of data for long distances without consuming too much energy, making it ideal for large-scale monitoring of the environment, tracking the location of people and objects, as well as collecting information on smart water/electric meters of public utilities, and many more. The chart below shows the differences between LoRa, Sigfox and NB-IoT.
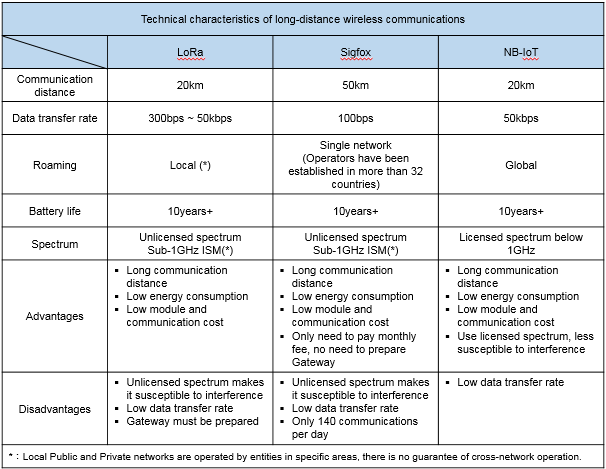
Differences between long-distance wireless communications
The bottleneck that IoT faces is the inability to communicate between different network communication technologies. So to allow successful communication between different wireless communication protocols, such protocols need to be integrated with the help of heterogeneous gateways through heterogeneous networks technology (see figure “The relationship between long- and short-distance wireless communications and battery consumption”). For example, the short-distance wireless technology networks used in the actual monitoring environment, such as Wi-Fi, Bluetooth and ZigBee, need to be able to communicate with the long-distance wireless technology networks, such as LoRa, Sigfox and NB-IoT. Most of the gateways seen today on the market are compatible with several communication technologies (such as Wi-Fi, Bluetooth, and ZigBee) to ensure successful communications.
III.Key technologies in application layer
Within the application layer, there are two protocols that are gradually becoming the mainstream in terms of Low Power Wide Area (LPWA). The first protocol is Message Queuing Telemetry Transport (MQTT), which works according to the TCP/IP protocol. It is to ensure that the connection with the receiving end device can be successfully established. The Transmission Control Protocol (TCP) can provide stable control, so that the data packets can be transmitted in sequence, be reassembled when they reach destinations, and have errors corrected. When reception is completed, the connection is closed smoothly. The drawback is that a large number of data packets are exchanged between the transmitting end and the server, which increases energy consumption. Most IoT technology vendors adopt this protocol. The second protocol is User Datagram Protocol (UDP), which does not establish a connection in advance, nor does it ensure that data packets can be transmitted in sequence and successfully received. Therefore, there is no guarantee that all data packets will be successfully transmitted. Even if they have been received completely, it is impossible to recover lost data packets and detect duplicate data packets. The advantage, however, is that there is no need to exchange a large number of data packets between the transmitting end and the server, thus saving energy. So in an IoT platform, the information is first collected by the sensing layer, then uploaded to the cloud platform of the application layer with wireless transmission technologies from the network layer. There, data statistics and analyses are performed so that users can make correct decisions. In terms of platform types, there are roughly three categories: cloud-based, network-based, and hardware-based. The above is an introduction to the basic concepts of IoT’s key technologies, which will be beneficial in understanding how CTCI applies IoT in construction sites, as described in the next section.
Smart site management becomes reality
In a construction work environment, given the considerable differences in terms of personnel access, distribution, and nature of work, it is important to have timely knowledge on the status of all on-site personnel to avoid safety issues and delays. One way of managing personnel movement smartly is to develop a site personnel positioning system, which uses fixed Bluetooth beacons that emit signals to detect the positions of ID card-wearing personnel, then sends the positioning information through radio waves back to the system. That way, managers can get hold of staff’s positions, build electronic fences, find specific staff right away, get hold of attendance records in a smart way, understand working hour statistics, monitor staff behaviors, receive distress signals, and see historical trajectories. This would greatly improve site management efficiency, maintain the order of on-site personnel, and ensure that on-site constructions can be carried out in an orderly fashion, thus truly achieving intelligent management. At CTCI, we adopted LoRa of LPWA (long-distance wireless communication network) plus Bluetooth technologies (short-distance wireless communication network). We also built a cloud-based platform called Location Mapping System (LMS) that allows users obtain necessary useful information to facilitate management work. Parallel testing has been conducted at the construction site, as explained below. In our parallel test, we placed Bluetooth beacons that continuously transmitted signals containing beacon number at intervals of 10 meters in a place where staff positions were to be calculated. The staff carried ID cards that were used for identifying their positions. Then the beacon numbers and strength information (RSSI) of the Bluetooth signals from those cards were collected and transmitted through LoRa signals to the gateway installed in the plant. Next, the gateway sent the data to the back-end positioning system server in 4G mode, so that the back-end server could get the positions of the beacons based on the geographic data entered when the beacons were first installed (refer to the system architecture figure below). Based on the strengths of the Bluetooth signals, we could calculate the possible distance between the Bluetooth beacons and ID card. Once we knew multiple beacon positions as well as the possible distances, we could then calculate the exact position of the ID card on a map by employing three-point fix method (shown in figure below: principle of positioning).
To make this method work, we needed to program several applications that can:
a)Retrieve the time data of personnel access through backend data API. b)Transform the alarm signal sent by the backend alarm API into LINE messages. The following figure describes the structure and principle of the personnel positioning system.
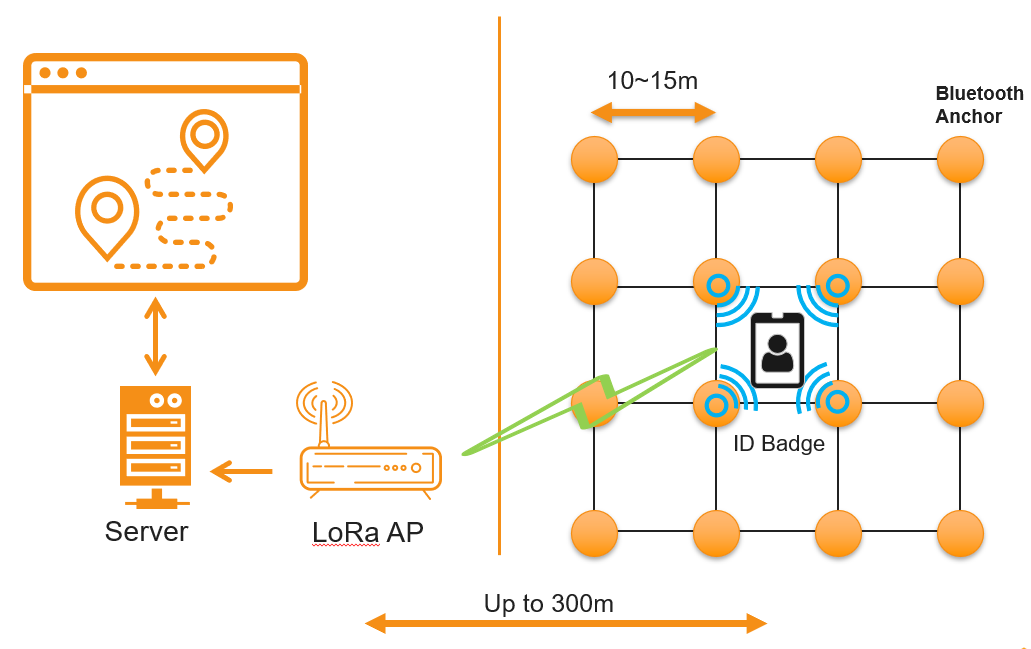
System structure
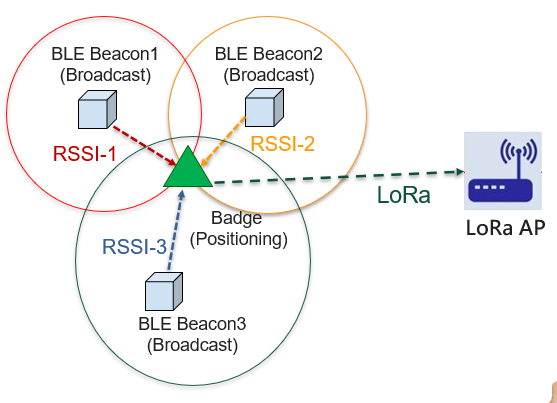
Positioning principle
After a series of tests, observations, adjustments, and verifications, we can now get an accurate and real-time picture of the positions of all personnel in a site. Thanks to technology, we now have better site and personnel management. With personnel position trajectory data and work location data, we can have a far more accurate understanding on when staff get to work and when they get off work than conventional clock-in data. This can help minimize disputes caused by forgetting to clock-in. Moreover, personnel trajectory records will be used for future big data analysis to help optimize project progress and manpower scheduling, as well as improve project progress and staff efficiency. In addition, managers can now be notified with alerts through LINE app or web platforms on their smartphones, which is more practical in a construction site environment. In this parallel test project, we used a virtual machine on the cloud service platform as the back-end server for personnel positioning, which carried out various functions such as position calculation, track recording, data statistics, and web interface display. The figure below shows what the web interface and personnel positioning system look like when indicating the exact positions of personnel in real-time.
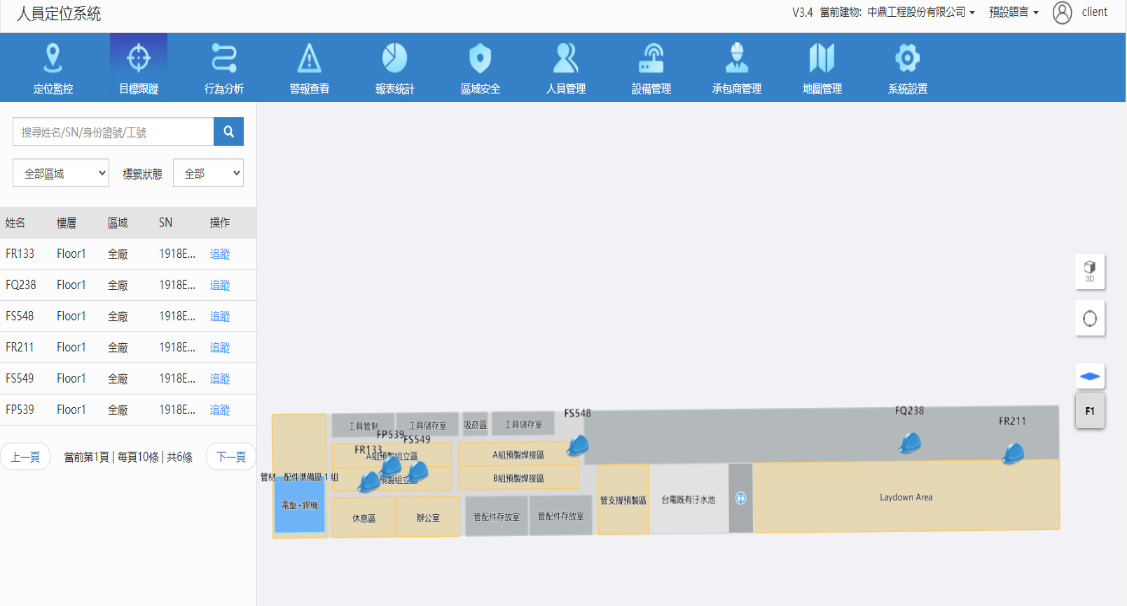
Webpage showing the Location Mapping System’s user interface
The Location Mapping System allows users to search for personnel’s past footprints. The results is displayed on the web page, a convenient way of looking into personnel's work status and carry out behavioral safety assessment, as shown in the figure below.
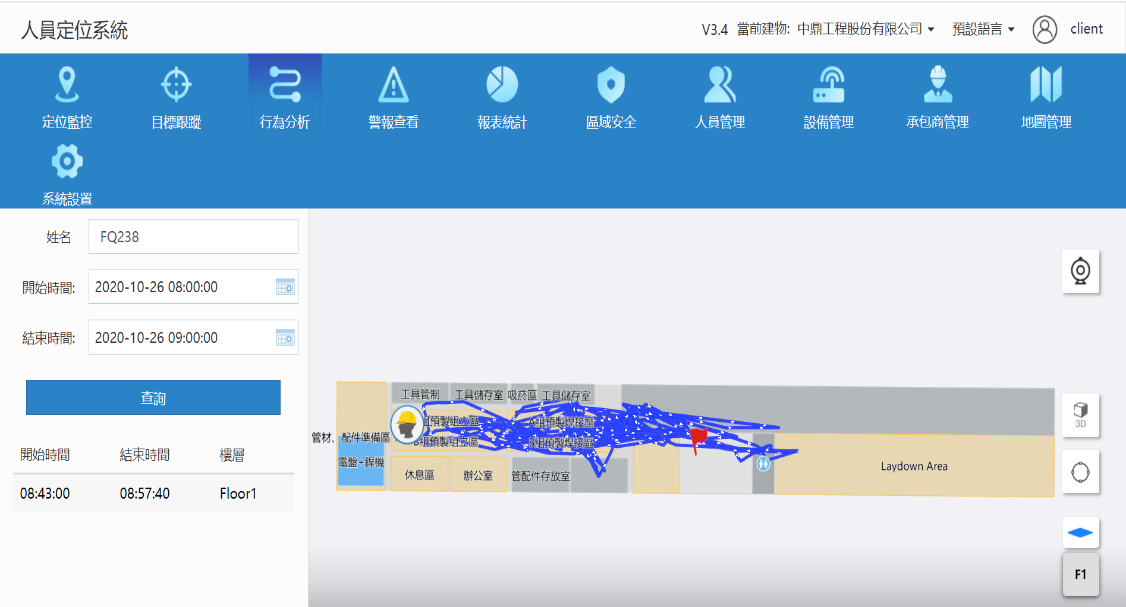
The system allows searching personnel’s past footprints
The figure below shows that by setting up a digital fence in a specific area, alerts will be triggered whenever people come inside the area or leave the area. This helps safely manage personnel in dangerous areas.
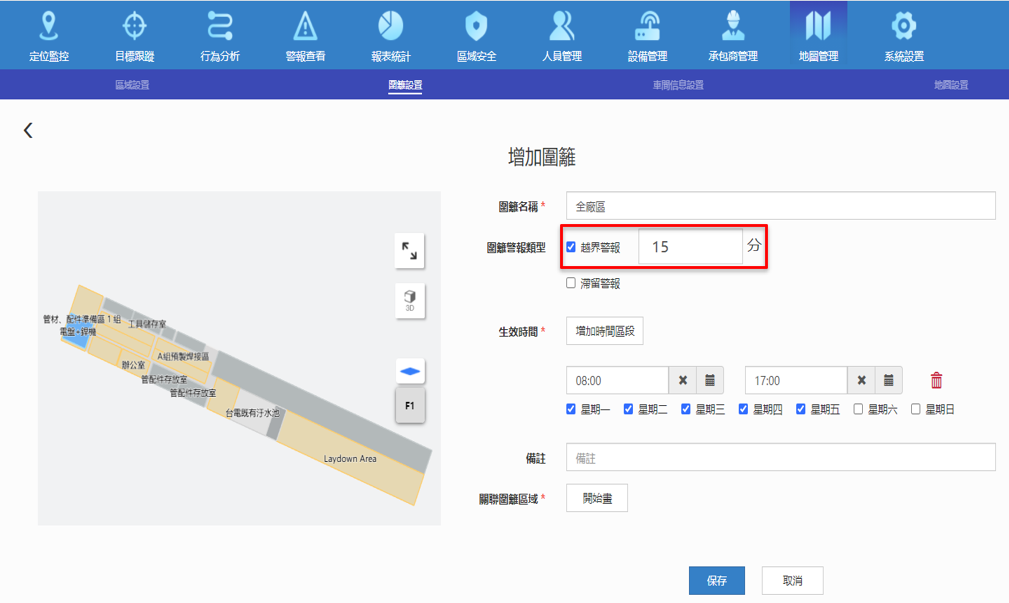
The system allows users to set alert criteria
Users can also decide how long they wish personnel to remain immobile before triggering the alert. Once the time is set, an alert will be triggered if a person remains immobile more than the amount of time allowed. This ensures timely rescue for anyone that passes out onsite.
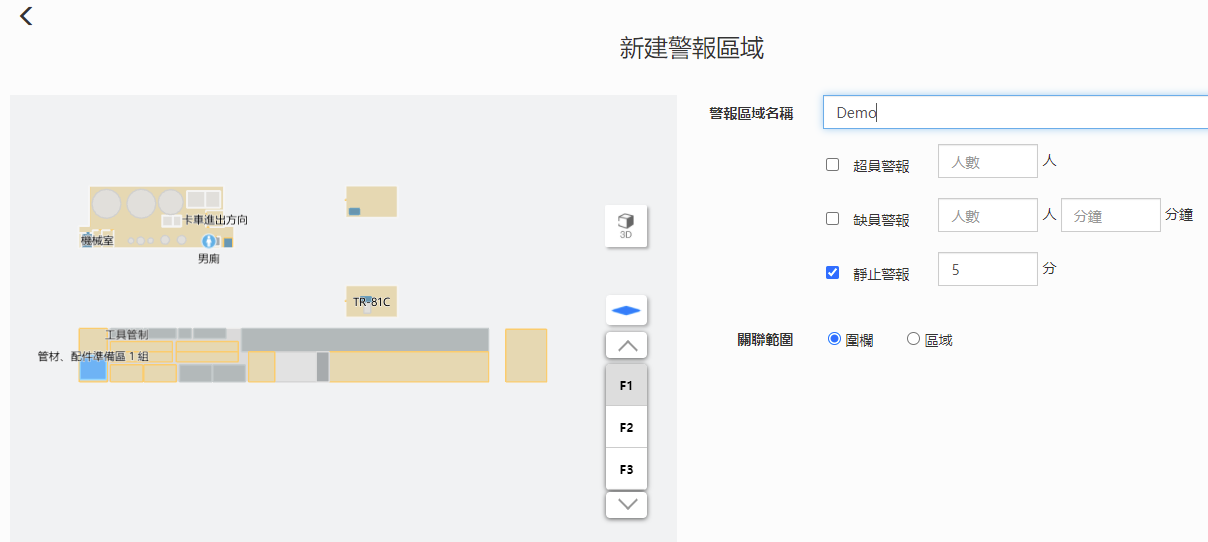
The immobile personnel alert function
Alerts are sent out through LINE app or web platforms on smart phones, which is more practical in a construction site environment. See figure below.
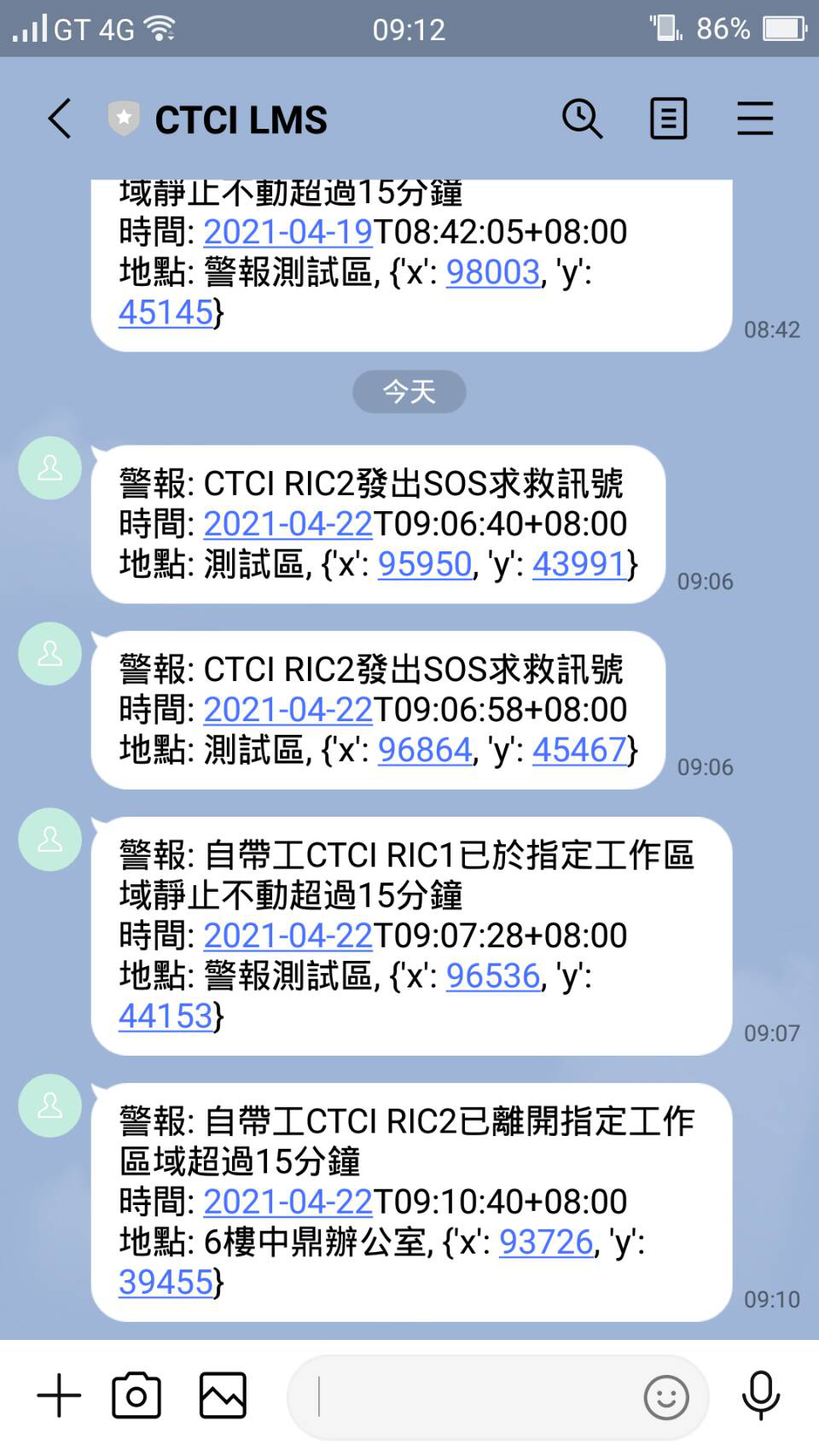
There are three types of alert messages sent through LINE app
Thanks to all these functions, we were able to establish a scope of warning for dangerous areas at construction sites and minimize unintentional entry by personnel, which in turn minimizes the chance of accidents and improves work safety. The immobile personnel alert function and real-time location information can allow timely awareness and rescue. If the person who is immobile remains conscious, he or she can press a SOS button and ask for help. This system, which is still under development by CTCI Group Research & Innovation Center, will be deployed at project sites once done.
Potential applications that IoT brings to construction sites
Construction sites are filled with dangerous facilities. Often times, safety incidents occur due to distraction or negligence— something that no one wishes to see, be it the victim, the victim’s families, or the company. Therefore, using LMS to conduct site management safely may be necessary. The following figure shows a potential way of managing sites with LMS, after discussing with the construction department fellows. For example, Bluetooth beacons can be set up at around places where there are holes in the ground or heavy parts are being hoisted. Next, determine safety distances through the back-end platform, so as to form a restricted area surrounded by electronic fence. At the meantime, all personnel on construction sites must wear ID cards to show their positions. Once they step into the restricted area, sound and lighting alert devices will be triggered, and a notice will be sent to the back-end platform and managers’ mobile devices.
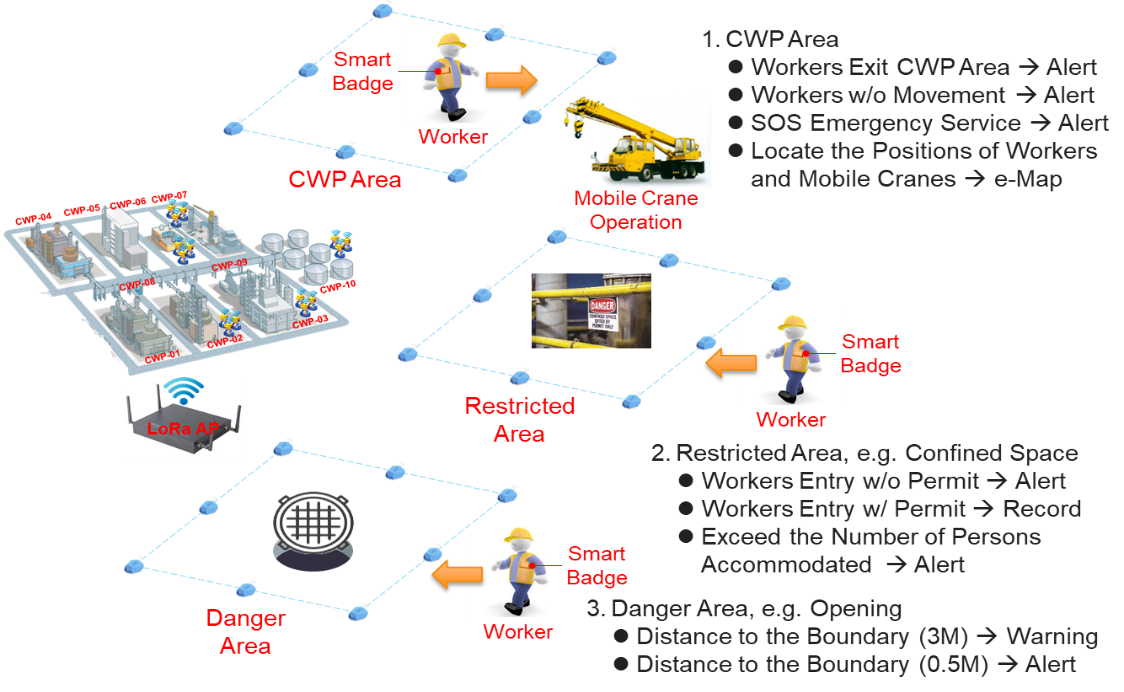
Other potential ways of applying LMS at construction sites
Conclusion
IoT’s wireless environment is a complex and diverse issue, which involves different transmission technologies, interconnection of heterogeneous wireless communication networks, and sensor battery performance, to name a few. It is no less complex than the construction environment of a work site. The implication is that to ensure successful adoption of IoT at construction sites, it requires thorough consideration and meticulous planning with regard to the initial overall wireless communication network architecture, the limitations of the construction site environment, and user needs. It is also indispensable to carry out on-site investigations. This article has only touched on the typical IoT practices. It should be noted, however, that IoT has gradually shifted towards 5G + AIoT in recent years, i.e., by combining 5G, AI, edge and cloud applications with typical IoT. A typical IoT uses sensors to collect perceived changes in a monitored person or an object before converting it into electrical signals (Edge) through preliminary calculations, and then use radio technology to return the signals to the back-end platform (Local), where the data is compared against standard values or behavior patterns. After the calculation, the correct parameters are sent to modify the operation mode of the person or object in question, and then present the most suitable behavior. However, elements such as AI, Edge and 5G are absent during this process. AIoT, on the other hand, brings in AI, Edge, and 5G elements, so that independent thinking and computing becomes possible. It is even capable of creating problem-solving skills with low latency. A typical example is driverless car technology. Perhaps in the near future, we will see a widespread application of typical IoT and AIoT technologies in construction site management, solving the obstacles and difficulties that we face in management today.
